Part 2: FPGAs | Hardware Acceleration of FHE
Fully Homomorphic Encryption (FHE) is one of the most exciting developments in cryptography, allowing computations on encrypted data without ever decrypting it. But there's a catch—it’s incredibly slow. Without specialized hardware, running homomorphic operations can be thousands of times slower than regular computations. This is where Field-Programmable Gate Arrays (FPGAs) come in. Their ability to handle parallel processing and custom logic makes them a great candidate for accelerating FHE, bringing it closer to real-world usability.
What Makes FPGAs Special?
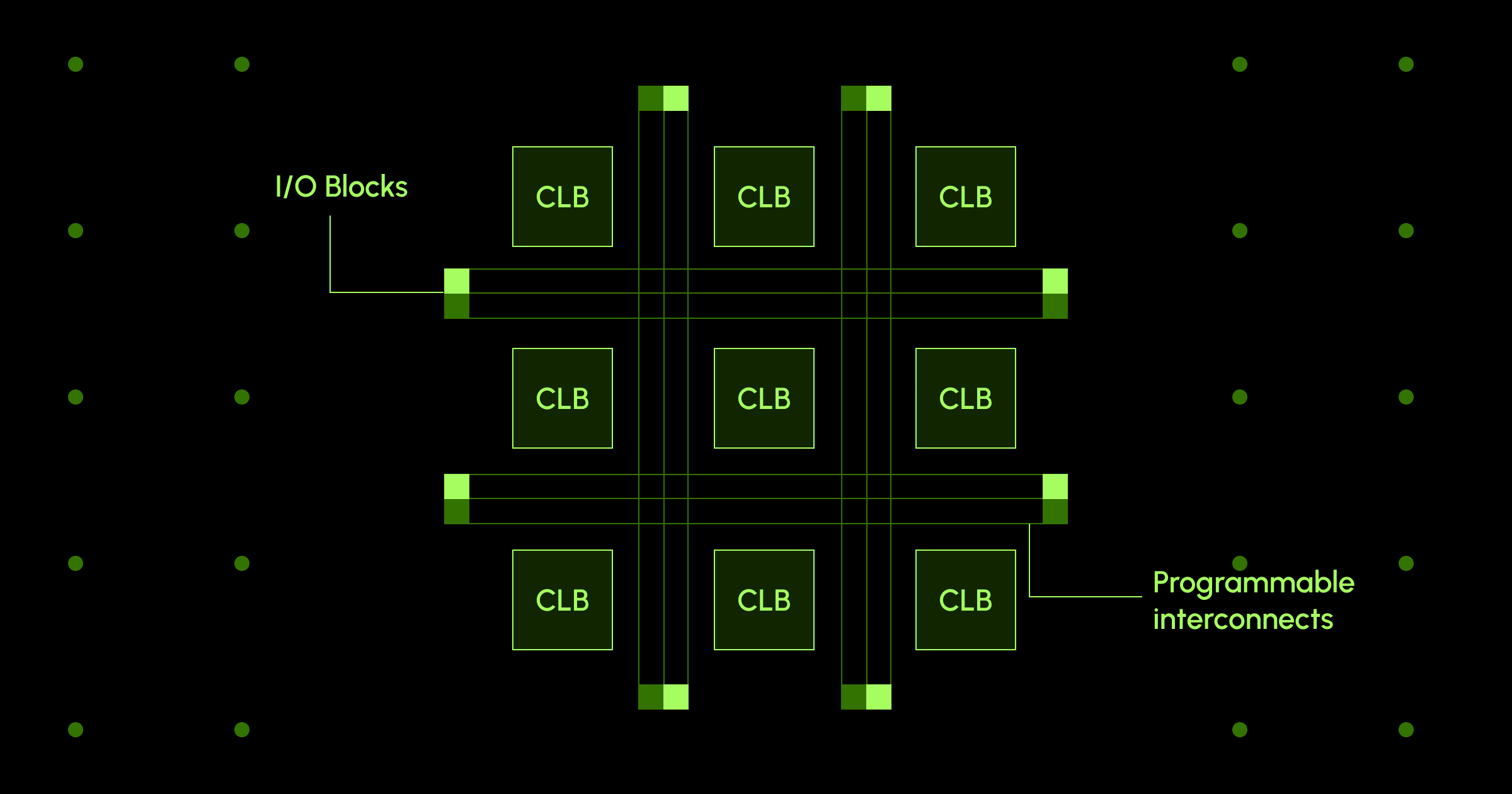
At their core, FPGAs work differently from traditional processors. Unlike CPUs, which execute instructions sequentially, an FPGA provides a sea of reconfigurable logic blocks and interconnects, allowing the creation of custom hardware circuits optimized for specific tasks. This flexibility enables FPGAs to handle complex cryptographic computations more efficiently than general-purpose hardware.
The heart of an FPGA consists of Configurable Logic Blocks (CLBs), each containing Look-Up Tables (LUTs) for implementing logical functions and flip-flops for storing state. These elements are connected via a programmable interconnect network, forming the foundation for high-speed, parallel processing. FPGAs also come equipped with Digital Signal Processing (DSP) blocks, which excel at performing arithmetic operations like multiplication and addition—critical for cryptographic applications. Additionally, they include various memory blocks, such as Block RAM (BRAM) and UltraRAM (URAM), which provide low-latency data storage to support high-performance computation.
One of the standout features of FPGAs is their ability to perform operations in parallel rather than sequentially. This is a game-changer for cryptographic workloads, where multiple independent operations can be executed simultaneously, dramatically improving performance. Unlike GPUs, which also offer parallelism but are constrained by fixed architectures, FPGAs allow for hardware-level customization, leading to highly efficient implementations of cryptographic algorithms.
Why Are FPGAs Ideal for FHE?
FHE schemes like BGV, BFV, and CKKS require heavy polynomial arithmetic and modular reductions over large numbers—operations that are notoriously slow in software. By leveraging the parallelism and customizable architecture of FPGAs, these computations can be significantly accelerated.
A critical component of FHE is the Number Theoretic Transform (NTT), which is used to speed up polynomial multiplication. Implementing NTT efficiently on FPGAs enables polynomial operations to run much faster than on CPUs by processing multiple elements in parallel. Another major bottleneck in FHE is bootstrapping—the process of refreshing noisy ciphertexts to maintain correctness over multiple operations. FPGA architectures allow for dedicated pipelines to optimize bootstrapping, reducing its overhead and making FHE computations more practical.
Memory management is another aspect where FPGAs shine. Homomorphic encryption involves manipulating large ciphertexts, which must be efficiently stored and retrieved to avoid performance bottlenecks. FPGAs, with their on-chip BRAM and URAM, can optimize data access patterns, reducing memory latency and improving throughput. This combination of efficient computation and memory access makes FPGAs an excellent fit for accelerating FHE workloads.
Implementation Challenges
Despite their strengths, FPGAs introduce unique challenges when applied to FHE. The first issue is resource constraints—large FHE computations require significant logic resources, DSP slices, and memory. Choosing an FPGA with enough capacity is crucial to avoid bottlenecks. Another challenge is balancing latency and throughput. Some optimizations reduce the delay per operation but may limit the overall number of operations that can be performed simultaneously, requiring careful architectural trade-offs.
Developing FPGA-accelerated cryptographic applications also requires specialized expertise. Unlike software development, where algorithms are written in high-level languages, FPGA programming typically involves Hardware Description Languages (HDLs) like Verilog or VHDL. This adds a layer of complexity, as developers must think in terms of hardware logic rather than sequential execution. Additionally, power and heat management are essential considerations, as high-performance FPGA implementations can generate significant heat, requiring effective cooling solutions to maintain stability.
Real-World Implementations
Recent FPGA-based FHE accelerators have demonstrated impressive performance improvements. For instance, implementations using Xilinx UltraScale+ FPGAs have achieved homomorphic multiplication speeds that are orders of magnitude faster than their CPU-based counterparts. Some architectures leverage PCIe-based FPGA accelerators, allowing cloud-based offloading of FHE computations to specialized hardware.
These real-world implementations highlight a few critical design strategies. Optimized NTT pipelines significantly speed up polynomial multiplications, while dedicated modular arithmetic units reduce the overhead of cryptographic operations. Some researchers are also exploring multi-FPGA architectures, distributing computations across multiple FPGAs to handle larger workloads and scale performance.
Security Considerations
With great computational power comes security risks. FPGA-based cryptographic implementations must be designed to resist side-channel attacks, which attempt to extract secret information by analyzing power consumption, timing, or electromagnetic emissions. One key defense is constant-time execution, ensuring that computation time remains consistent regardless of input values. Additionally, power analysis resistance techniques, such as masking and randomization, help prevent attackers from deducing secret keys through power measurements. Fault injection protection is also critical, as attackers may try to manipulate computations by introducing errors into the FPGA’s logic.
What’s Next?
While FPGAs have already shown promising results in accelerating FHE, there’s still plenty of room for improvement. One major area of focus is better memory optimization, particularly using hybrid FPGA architectures with High Bandwidth Memory (HBM) to accommodate the growing data requirements of FHE computations. Another avenue of research involves scaling multi-FPGA solutions to distribute workloads even more effectively.
Ultimately, while FPGAs are currently the best solution for accelerating FHE, the future may see a transition toward dedicated ASICs (Application-Specific Integrated Circuits). ASICs, unlike FPGAs, are designed for a specific function from the ground up, offering performance and energy efficiency. However, the flexibility of FPGAs ensures they will remain a crucial stepping stone in the journey toward practical homomorphic encryption.
Conclusion
FPGAs are proving to be one of the key solutions for making FHE more practical, providing significant speedups over traditional CPU-based approaches. By leveraging their parallel processing, customizable logic, and memory optimization capabilities, they are helping to bridge the gap between theoretical cryptography and real-world applications. While challenges remain, continued advancements in FPGA architectures and optimization techniques are pushing the boundaries of what’s possible in confidential computing.
If you are interested more, you can take a look at this presentation during FHE Summit Brussels 2024
Subscribe to our newsletter
Top industry insights on FHE.
.svg)
